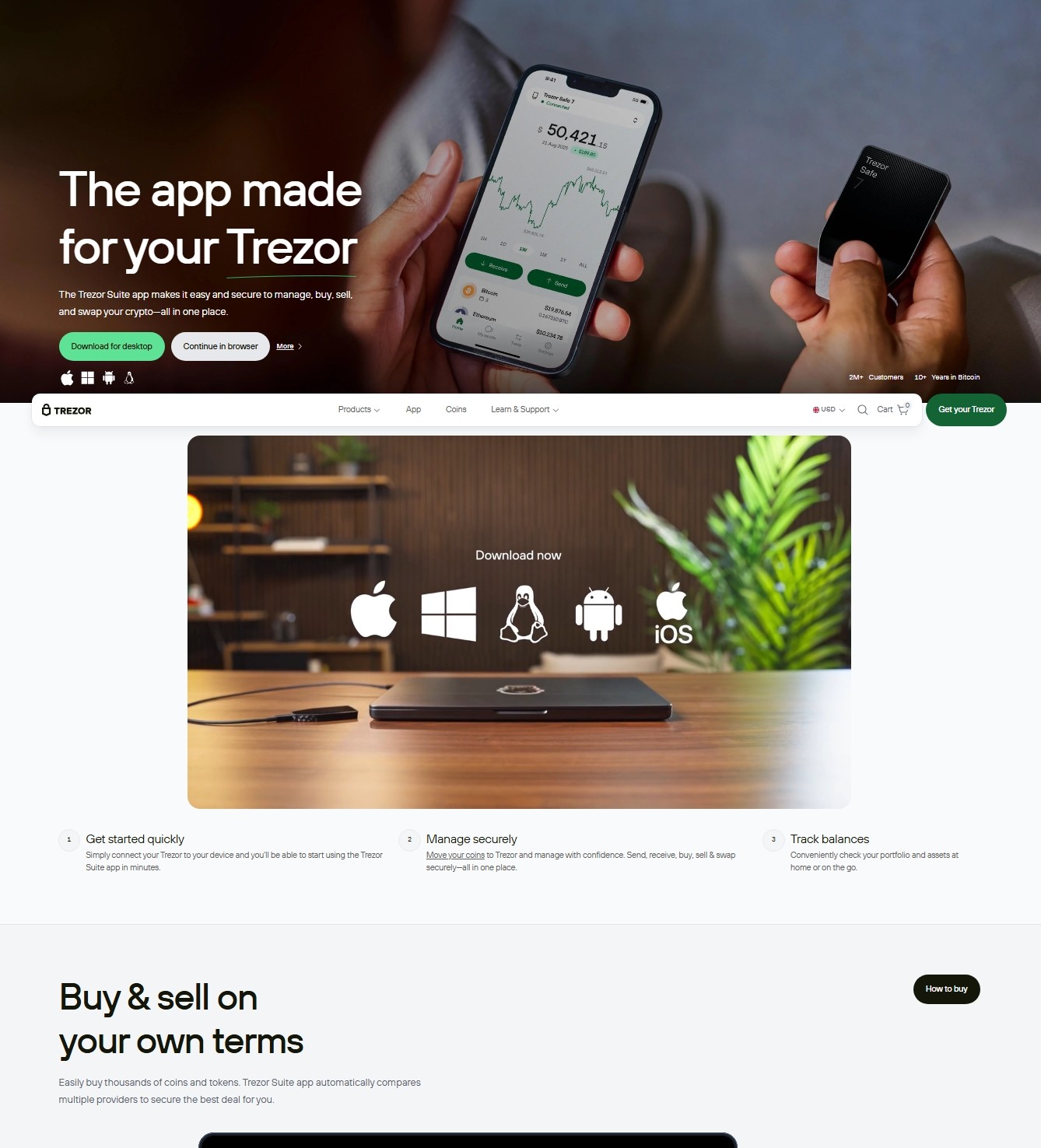
Trezor.io/Start: Your Gateway to Secure Cryptocurrency Management
In the rapidly evolving world of cryptocurrencies, security is more than a priority—it’s a necessity. As digital assets become increasingly mainstream, the need for a secure, reliable, and user-friendly method to store, manage, and transact cryptocurrencies has never been more pressing. That’s where Trezor steps in.
Trezor is a pioneering leader in the realm of cryptocurrency hardware wallets, designed to give users complete control over their digital assets while providing robust protection against digital threats. By visiting Trezor.io/Start, users can embark on a seamless journey toward enhanced crypto security, whether they are seasoned investors or new to the world of blockchain.
Why Security Matters in Crypto
The decentralized nature of cryptocurrencies is both a blessing and a challenge. While blockchain technology ensures transparency and immutability, it also places the responsibility of asset protection squarely in the hands of the user. Unlike traditional banks, cryptocurrencies are not insured or protected by a central authority. Losing access to your private keys or falling victim to phishing attacks can result in permanent loss of funds.
This is precisely why hardware wallets like Trezor have become essential. Unlike software wallets or exchanges that store private keys online, Trezor devices store them offline, ensuring that your funds remain safe from hackers, malware, and other cyber threats.
Getting Started with Trezor
Starting your journey with Trezor is simple and intuitive. By visiting Trezor.io/Start, you can follow a straightforward setup process that ensures your assets are protected from day one.
Step 1: Choose Your Trezor Device
Trezor offers a range of hardware wallets tailored to different user needs. Whether you’re looking for the entry-level Trezor One or the feature-rich Trezor Model T, there’s an option for everyone. Each device is designed to be user-friendly, with clear instructions and robust security features.
Step 2: Connect and Initialize Your Device
Once you have your Trezor device, connect it to your computer using the supplied cable. The device will guide you through the initialization process, which includes creating a secure PIN and generating a recovery seed—a series of words that act as a backup for your wallet.
Step 3: Secure Your Recovery Seed
The recovery seed is the key to restoring your wallet if your device is lost or damaged. It’s essential to write it down on the provided card and store it in a safe, offline location. Avoid taking photos or storing it digitally, as this can compromise your security.
Step 4: Access the Trezor Wallet Interface
With your device initialized, you can now access the Trezor Wallet interface. This web-based platform allows you to manage your cryptocurrency portfolio, send and receive funds, and monitor transactions—all from the safety of your offline hardware wallet.
Login Button Placement Suggestion:
Features That Set Trezor Apart
Trezor’s popularity is not accidental. The platform is built around a philosophy of security, usability, and transparency, offering features that cater to both beginners and experienced crypto enthusiasts.
1. Ultimate Security
Trezor wallets use advanced cryptography and offline key storage to protect assets. Even if your computer is compromised, your private keys remain secure inside the hardware device.
2. Multi-Currency Support
Trezor supports hundreds of cryptocurrencies, including Bitcoin, Ethereum, and a growing number of altcoins. This versatility allows users to manage diverse portfolios from a single, secure interface.
3. User-Friendly Interface
The Trezor Wallet interface is intuitive and accessible. Detailed transaction history, real-time portfolio tracking, and simple send/receive functions make managing digital assets straightforward—even for newcomers.
4. Backup and Recovery Options
With Trezor, users can rest easy knowing that their funds are recoverable. The recovery seed system ensures that even in the event of device loss, funds can be restored quickly and securely.
5. Open-Source Transparency
Trezor’s firmware is open-source, allowing security experts worldwide to audit and verify the integrity of the software. This commitment to transparency fosters trust and ensures that vulnerabilities are identified and resolved promptly.
Security Best Practices for Trezor Users
While Trezor provides world-class security, users play a crucial role in protecting their assets. Here are some best practices to follow:
Never share your PIN or recovery seed. No legitimate entity will ever ask for this information.
Verify URLs carefully. Only access wallet.trezor.io or trezor.io for official operations.
Keep firmware updated. Regular updates ensure your device benefits from the latest security enhancements.
Use a passphrase. Trezor allows users to add an extra layer of security with a passphrase in addition to the recovery seed.
Following these guidelines ensures that your digital assets remain secure, even in a landscape filled with phishing attacks and sophisticated cyber threats.
Why Trezor is the Choice for Professionals and Enthusiasts
Trezor is more than a hardware wallet—it’s a comprehensive solution for managing digital wealth safely. Professionals who handle significant amounts of cryptocurrency trust Trezor for its unmatched security features, ease of use, and commitment to transparency.
Even beginners can feel confident using Trezor. The setup process is guided and straightforward, while educational resources help users understand cryptocurrency security concepts, empowering them to manage their assets responsibly.
Integrating Trezor Into Your Crypto Strategy
Managing cryptocurrency effectively requires more than just storage—it demands a strategic approach. Trezor’s tools and integrations allow users to incorporate their wallets into broader crypto strategies:
Trading: Safely transfer funds between exchanges while keeping the majority of assets offline.
Staking: Participate in staking programs supported by Trezor without compromising security.
Portfolio Management: Track multiple assets and transaction histories in a single, consolidated view.
By combining security with functionality, Trezor enables users to take full advantage of the opportunities within the crypto ecosystem.
Getting Started Today
Starting your journey with Trezor is simple and secure. Visit Trezor.io/Start and follow the step-by-step guide to initialize your device, set up your wallet, and take control of your digital assets.
Login Button Placement Suggestion:
With Trezor, you don’t just store cryptocurrency—you gain peace of mind, knowing that your digital assets are protected by world-class security, transparency, and user-centered design.
Conclusion
In a world where digital threats are constantly evolving, securing your cryptocurrency is paramount. Trezor offers an intuitive, reliable, and highly secure solution that empowers users to take full control of their assets. From beginners to seasoned investors, Trezor provides the tools, education, and infrastructure necessary for confident, secure crypto management.
Visit Trezor.io/Start today, set up your wallet, and experience a new standard in cryptocurrency security. Your assets deserve nothing less than the protection Trezor offers.